 |
 |
|
 |
|
 |
|  |
|  |
|
 |
|
 |
|  |
|  |
|
 |
>> http://en.wikipedia.org/wiki/Eicar_test_file
>
> Haha, thanks Jim, I didn't know that existed. You guys are great.
Well it's a lot safer than "keeping a collection of real viruses for
test purposes". ;-)
--
http://blog.orphi.me.uk/
http://www.zazzle.com/MathematicalOrchid*
Post a reply to this message
|
 |
|  |
|  |
|
 |
|
 |
|  |
|  |
|
 |
Orchid XP v8 wrote:
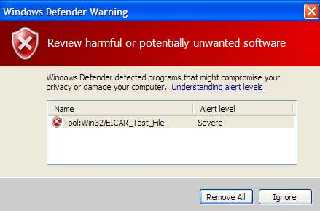
> X5O!P%@AP[4\PZX54(P^)7CC)7}$EICAR-STANDARD-ANTIVIRUS-TEST-FILE!$H+H*
>
I'm impressed! Defender actually picked this up. Who knew it had virus
definitions ...
Post a reply to this message
Attachments:
Download 'defender.jpg' (17 KB)
Preview of image 'defender.jpg'
|
 |
|  |
|  |
|
 |
|
 |
|  |
|  |
|
 |
Mike Raiford wrote:
> I'm impressed! Defender actually picked this up. Who knew it had virus
> definitions ...
LOL @ threat level.
--
http://blog.orphi.me.uk/
http://www.zazzle.com/MathematicalOrchid*
Post a reply to this message
|
 |
|  |
|  |
|
 |
|
 |
|  |
|  |
|
 |
On Wed, 06 Aug 2008 08:59:31 +0100, Invisible wrote:
>>> http://en.wikipedia.org/wiki/Eicar_test_file
>>
>> Haha, thanks Jim, I didn't know that existed. You guys are great.
>
> Well it's a lot safer than "keeping a collection of real viruses for
> test purposes". ;-)
Depends on what you want to test. I was using it to test virus
interaction with software; the Eicar test file isn't particularly useful
for that.
But that's another thing that virtualization is great for - sandboxing
for that sort of testing.
Jim
Post a reply to this message
|
 |
|  |
|  |
|
 |
|
 |
|  |
|  |
|
 |
"Invisible" <voi### [at] dev null> wrote in message
news:4896fdf4$1@news.povray.org...
>
> All the big names are there - Byte Bandit, Chynoble, Melissa, Code Red,
> SQL Slammer, Sobig, Sober, MyDoom, MS Blaster, Klez, Nachi, etc. Plus
> there's a few I haven't even heard of. (Obviously most of these are PC
> viruses, and it wasn't until the late 90s that I started using that
> platform.)
The interesting (and unfortunate) thing about SQL Slammer is that the patch
that closed the exploit had been released a couple of months before the worm
appeared. The reason is was so widespread is that most organisations hadn't
bothered applying any service packs null> wrote in message
news:4896fdf4$1@news.povray.org...
>
> All the big names are there - Byte Bandit, Chynoble, Melissa, Code Red,
> SQL Slammer, Sobig, Sober, MyDoom, MS Blaster, Klez, Nachi, etc. Plus
> there's a few I haven't even heard of. (Obviously most of these are PC
> viruses, and it wasn't until the late 90s that I started using that
> platform.)
The interesting (and unfortunate) thing about SQL Slammer is that the patch
that closed the exploit had been released a couple of months before the worm
appeared. The reason is was so widespread is that most organisations hadn't
bothered applying any service packs
Post a reply to this message
|
 |
|  |
|  |
|
 |
|
 |
|  |
|  |
|
 |
Gail Shaw wrote:
> The interesting (and unfortunate) thing about SQL Slammer is that the patch
> that closed the exploit had been released a couple of months before the worm
> appeared. The reason is was so widespread is that most organisations hadn't
> bothered applying any service packs
Indeed. Some of these things use a hole that was patched a week or two
ago, but some hit really "old" holes that were fixed ages ago.
OTOH, throwing an update onto a home PC is one thing. I guess you have
to be a tad more careful when it's a production-grade server we're
talking about...
(I don't know how SQL Slammer works, but wouldn't you have to have SQL
access exposed to the Internet for it to propogate?)
Ah well, at least I know why I keep getting all those strange entries in
my web logs... Apparently they're trying to exploit a bug in ISS. ;-)
--
http://blog.orphi.me.uk/
http://www.zazzle.com/MathematicalOrchid*
Post a reply to this message
|
 |
|  |
|  |
|
 |
|
 |
|  |
|  |
|
 |
Orchid XP v8 wrote:
> Gail Shaw wrote:
>
>> The interesting (and unfortunate) thing about SQL Slammer is that the
>> patch that closed the exploit had been released a couple of months before
>> the worm appeared. The reason is was so widespread is that most
>> organisations hadn't bothered applying any service packs
>
> Indeed. Some of these things use a hole that was patched a week or two
> ago, but some hit really "old" holes that were fixed ages ago.
I heard of a really interesting one. Microsoft found a security bug (or was
responsibly and privately notified of it by another company/individual). As
usual, on Patch Tuesday they released an update fixing it, along with other
updates.
Some motivated hacker *reverse-engineered the update*. He compared the
relevant DLL before and after the update, basically. And figured out what
the vulnerability was.
And proceeded to pwn unpatched machines.
Post a reply to this message
|
 |
|  |
|  |
|
 |
|
 |
|  |
|  |
|
 |
>> Well it's a lot safer than "keeping a collection of real viruses for
>> test purposes". ;-)
>
> Depends on what you want to test. I was using it to test virus
> interaction with software; the Eicar test file isn't particularly useful
> for that.
Surely this is going to vary arbitrarily for each individual virus?
--
http://blog.orphi.me.uk/
http://www.zazzle.com/MathematicalOrchid*
Post a reply to this message
|
 |
|  |
|  |
|
 |
|
 |
|  |
|  |
|
 |
Nicolas Alvarez wrote:
> Some motivated hacker *reverse-engineered the update*. He compared the
> relevant DLL before and after the update, basically. And figured out what
> the vulnerability was.
>
> And proceeded to pwn unpatched machines.
I'm told this is standard practice now... ;-)
--
http://blog.orphi.me.uk/
http://www.zazzle.com/MathematicalOrchid*
Post a reply to this message
|
 |
|  |
|  |
|
 |
|
 |
|  |
|  |
|
 |
On Thu, 07 Aug 2008 08:56:40 +0100, Invisible wrote:
>>> Well it's a lot safer than "keeping a collection of real viruses for
>>> test purposes". ;-)
>>
>> Depends on what you want to test. I was using it to test virus
>> interaction with software; the Eicar test file isn't particularly
>> useful for that.
>
> Surely this is going to vary arbitrarily for each individual virus?
Not necessarily. In my example of running WordPerfect from a networked
drive, the problem was reproducible every time. Infect machine, start up
WP, start doing work, WP starts creating massive temporary files on the
network drive until the space is used up.
Similarly, we had write-protected boot diskettes for the machines, but
the lab assistants would re-enable write by taping over the hole (3.5"
diskettes, we'd remove the write protect tabs on the boot diskettes) so
the diskette would get infected. Warm boot infected machine with write
protected diskette, you'd get a "write error" on boot every time. The
virus was actually coded to intercept a warm boot and keep itself in
memory while actually rebooting the machine, then would try to write
itself out to the boot diskette in order to spread.
Really strange to get a write protect error before DOS seemingly started
up.
Jim
Post a reply to this message
|
 |
|  |
|  |
|
 |
|
 |
|  |




![]()